
Attack on WordPress based websites through Duplicator files
In recent hours, on many pages based on WordPress, instead of the homepage there was a screen for the installation of this CMS. The problem was the lack of the wp-config.php file, which was removed.
On social networks, posts about disappearing WordPress files started to appear.
Spis treści
Podatność
After analysis on several servers, the vector of the attack were the files left after page migration using the Duplicator plugin. Example of an attack log on a website:
54.38.130.58 - - [06/Sep/2018:13:22:24 +0000] "POST /installer.php HTTP/1.1" 200 497 "example.pl/wp-admin/admin-ajax.php" "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1985.143 Safari/537.36"
54.38.130.58 - - [06/Sep/2018:13:22:24 +0000] "POST /installer-backup.php HTTP/1.1" 200 497 "example.pl/wp-admin/admin-ajax.php" "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1985.143 Safari/537.36"
54.38.130.58 - - [06/Sep/2018:13:22:25 +0000] "GET /wp-crawl.php?q=ZWNobyAiYmFyYmllZGVuIjs= HTTP/1.1" 200 9 "-" "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1985.143 Safari/537.36"
54.38.130.58 - - [06/Sep/2018:13:22:26 +0000] "GET /wp-content/uploads/wp-crawl.php?q=ZWNobyAiYmFyYmllZGVuIjs= HTTP/1.1" 200 9 "-" "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1985.143 Safari/537.36"An attacker using the left file installer.php (or installer-backup.php) is able to upload e.g. Trojan horses to the server and gain access to the files on the server and database. This is a Remote Code Execution error, which was also confirmed by Wordfence.
The vulnerability itself does not exist in the Duplicator plugin, but is in files that are generated to move the page to another server.
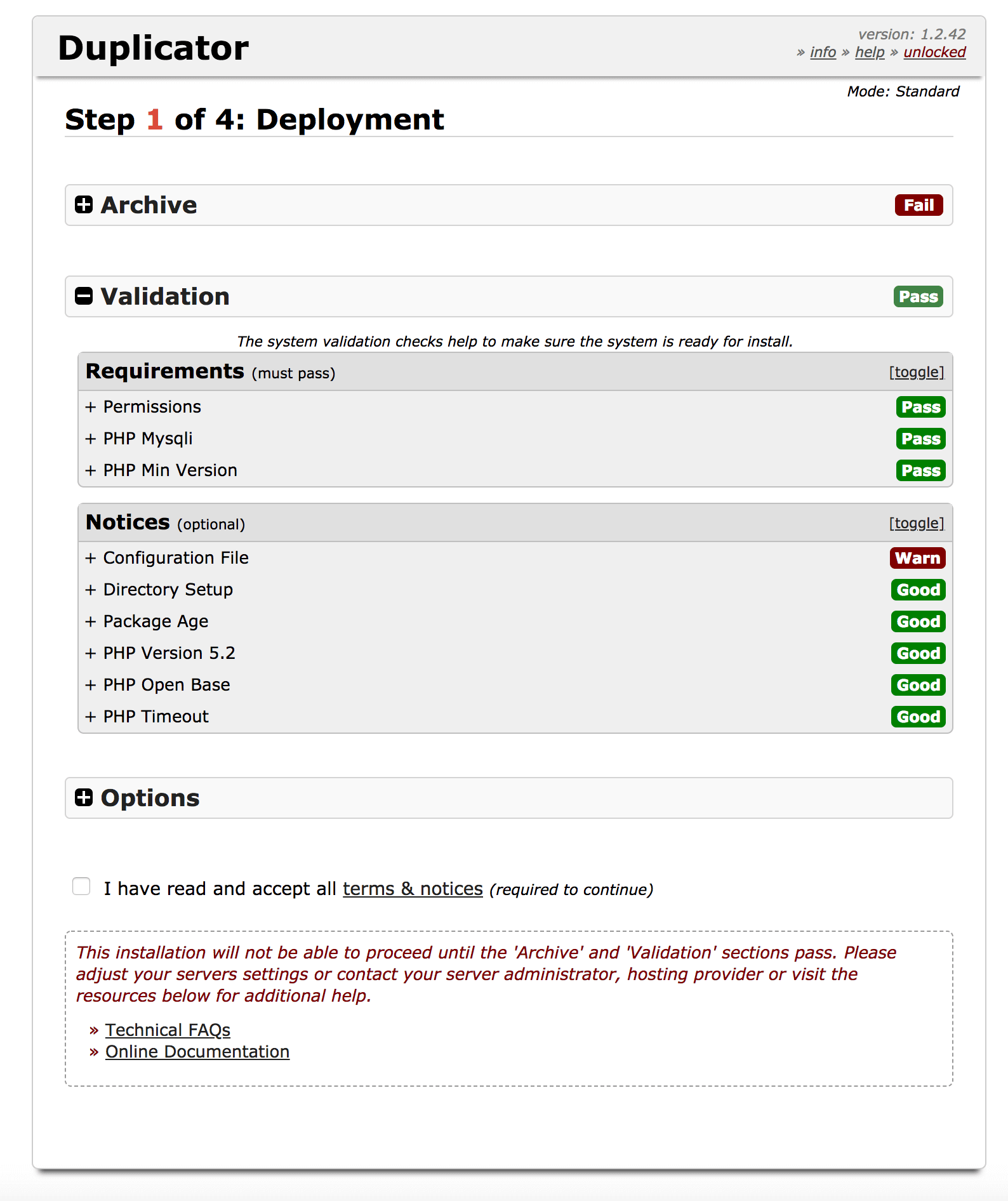
By passing the value of action_ajax=3 in the POST parameter, the attacker is able to bypass the file verification window and overwrite it wp-config.php.
In the next step, simply visit the attacked page to read the wp-config.php file, which already has malicious code.
What do attackers have access to?
If your server was cluttered, and what’s worse, the files created by Duplicator during website migration, the attacker has access to all data related to your website.
Sample files left after page migration using Duplicator:
- 20180906_examplepl_8b5c33bcbb1d027b1870180906225049_archive.zip
- installer-backup.php
- installer-data.sql
- installer-log.txt
- installer.php
The zip file contains a copy of all files on the a sql page, the database. After migration, all above mentioned files should be deleted.
How to protect yourself and what to do?
If an archive created by Duplicator has been downloaded, the attacker should be considered to have access to the database and files on the website. First of all, you should restore the page from backup and change all passwords related to it.
After migrating a page using Duplicator, delete all of its files. The plugin itself allows you to do this immediately after logging in to the WordPress admin panel.
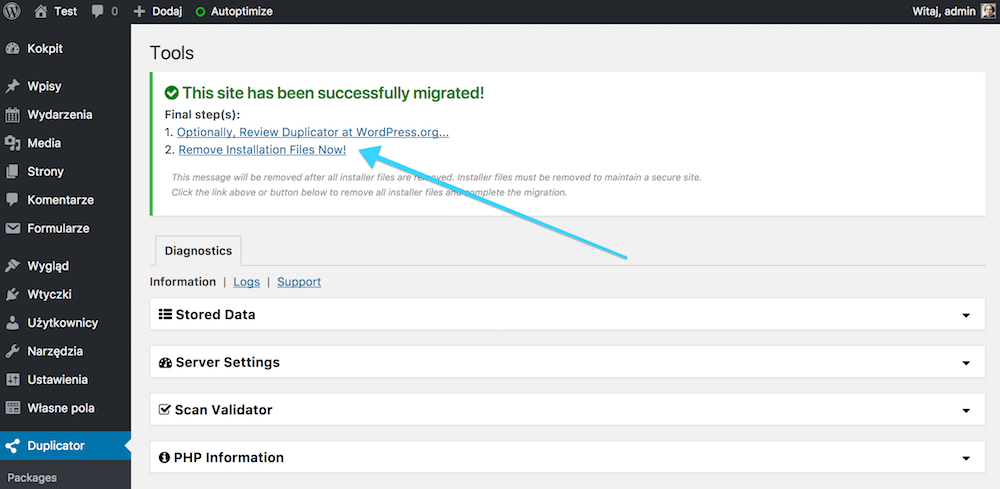
Click on the link: Remove installation Files Now! It is still worth checking if all installation files have actually been removed. In case of the attack described above, it could have been such that the files were not deleted due to an error in the plugin.
On our servers, these files have been deleted for security reasons.
If you have stored data for various services such as mail systems, newsletter data, etc. in WordPress, you also need to change your passwords there.
For detailed information about WordPress security, please refer to our compendium. We would like to remind you that using backup plug-ins can be very dangerous.
Check other blog posts
See all blog posts
6 April 2022
Why is it a good idea to split sites across different hosting accounts?
Read moreMultiple websites on one server is a threat that can have different faces. Find out what the most important ones are and see why you should split your sites on different hosting accounts. Powiązane wpisy: Compendium: how to secure your WordPress? Everything you have to keep in mind when creating an online store Useful plugins…

13 September 2021
How do you get your website ready for Black Friday or more traffic?
Read moreToo much website traffic can be as disastrous as no traffic at all. A traffic disaster results in server overload. In such a situation, no one is able to use e.g. your online store’s offer, and you do not earn. Learn how to optimally prepare your website for increased traffic. Powiązane wpisy: Compendium: how to…

10 September 2021
Password management or how not to lose your data
Read moreDo you have a bank account? Use the internet with your smartphone? Congratulations! Then you are on the brighter side of the power, where digital exclusion does not reach. But can you take care of the security of your data as effectively as you invite your friend for a beer via instant messenger? Powiązane wpisy:…
